Securing Process
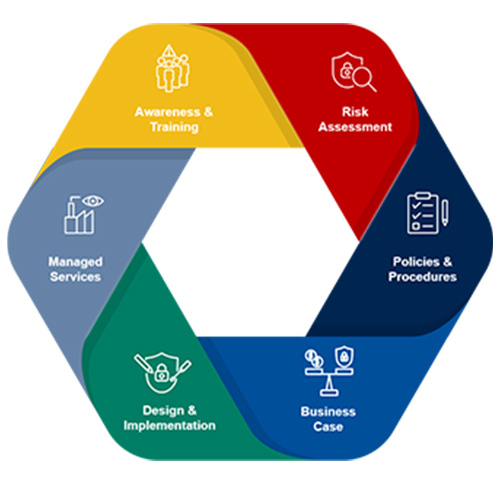
Securing Process.
Processes are the step-by-step guide that describes how things are done in the best possible way in the organization, thereby making it easy for people to focus on the major areas. Hence planning and managing key processes effectively and efficiently, not only reduces the risk to the business, but also enables organization to comply with the best methods, thereby ensures the success of the business.
Value
- Improved Efficiency and Effectiveness
- Reduced Process Risk
- Increased Reliability and Resilience
Strategy and Governance
Looking to align your IT and IS Objectives to your business goals and utilize good governance practices and Frameworks to derive better value and return.
Risk Management
Looking to develop a risk aware culture, enabling you to effectively identify, assess, evaluate, manage and mitigate technology risks to protect the assets and achieve the objectives.
Compliance
Looking to comply with global information security and data privacy standards, frameworks and regulations like, ISO 27001, ISO 27701, NIST, SOC1, SOC2, GDPR, DPDPA 2023, CCPA, HIPAA, PCI DSS, etc.
Incident Detection and Response
Looking to design, build, develop and deploy the plans, processes and solutions to monitor, detect and respond to the events and incidents including data leaks and data breaches in an effective and efficient manner.
Assessments / Audits
Looking for assurance for the organizational and technical measures, practices and controls built, vis-a-viz the business, contractual, legal and regulatory requirements to protect and safeguard your assets – People, Processes, Technology, Data and Things.
Third Party Risk Management
Looking to design, build, develop and deploy the practices, processes and controls to assess, evaluate, manage and mitigate the digital risks arising from the third parties and the supply chain.
Identity and Access Management
Looking to design, build, develop, deploy and manage the identity and access management processes, tools and solutions to effectively curb the menace of unauthorized access, use and misuse, and disclosure of information.
Business Continuity and Disaster Recovery
Looking to design, build, develop and deploy the effective and efficient plans, processes and solutions to ensure the continuity and the recovery of the business in the event of any disruptive incident or disaster.